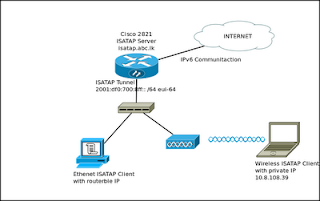
Here We have enabled ISATAP in our network to enable clients to access Internet through IPv6 communication. We have used the Cisco 2821 router as the ISATAP server and enabled Windows 7/ Windows XP clients to make tunnels with the ISATAP router (Which is the Cisco 2821 router) and get assigned a global IPv6 address.
The diagram shows an overview of the network.
Enabled ISATAP in ciscoconfigure terminal
!
interface Tunnel 100
ip address 2001:df0:17:8ff::/64 eui-64
no ipv6 nd suppress-ra
tunnel source 192.248.8.125
tunnel mode ipv6ip isatap
!
The ip address is the IPv6 IP address block that you are going to assign to the ISATAP clients. The first 64 bit will be the block that you define here and the remaining 64 bits will be filled as given in the
RFC 5214Use following commands to check the the status of the tunnel interface
show ip interface tunnel 100
show ipv6 interface tunnel 100
Configuring Windows 7/ XP clientsAs Windows 7 is inheritance IPv6 enabled, following commands will enable the ISATAP tunnel according to the setup;
Enabling ISATAP interface
netsh interface isatap set state enabled
Check the default router settings
netsh interface isatap show router
Set the ISATAP router
netsh interface isatap set router isatap.abc.lk
Enable ISATAP in WindowsXPFirst IPv6 should be enabled in the host OS using following commands
netsh interface ipv6 install
OR
you can install IPv6 using the GUI in following manner
- Open Network Connections
- Right-click any local area connection, and then click Properties.
- Click Install.
- In the Select Network Component Type dialog box, click Protocol, and then click Add.
- In the Select Network Protocol dialog box, click Microsoft TCP/IP version 6, and then click OK.
- Click Close to save changes to your network connection.
Reference http://www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/sag_ip_v6_pro_inst.mspx?mfr=true
After installing ipv6, the host is automatically enabled for isatap and 6to4 tunneling
To enable ISATAP interface and router use following commands
netsh interface ipv6 isatap set state enabled
netsh interface ipv6 isatap set router isatap.mrt.ac.lk
After setting the router, host will communicate with the router and get assigend ipv6 address from the isatap router
The ipv6 address assiged to the isatap interface has a direct relationship with the ipv4 address of the host.
Enable ISATAP in Ubuntu
The Ubuntu versions we have tested is 10.04 LTS
The isatapd deamon should be installed from apt-get install command and start the daemon with the ISATAP router parameters;
isatapd -r isatap.abc.lk &
The Ipv6 communications can be monitored using tcpdump -n ip6 command;
Following given is an observation of IPv6 communication
tcpdump -n ip6
Good references:
http://www.ciscosim.net/ipv6-transition-mechanisms-part-4-isatap-tunnels/9.htmlhttp://www.cisco.com/en/US/docs/ios/ipv6/configuration/guide/ip6-tunnel.html#wpxref21012
http://www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/sag_ip_v6_pro_inst.mspx?mfr=truehttp://measureofchaos.blogspot.com/2011/03/isatap-setup-on-windows-clients.html

